Connection Permissions
Data connections, through permission management and control, enhance data usability while safeguarding data security, enabling the system to function as a unified data publishing platform. This allows various business departments to access authoritative and unified data as needed.
Connection Management
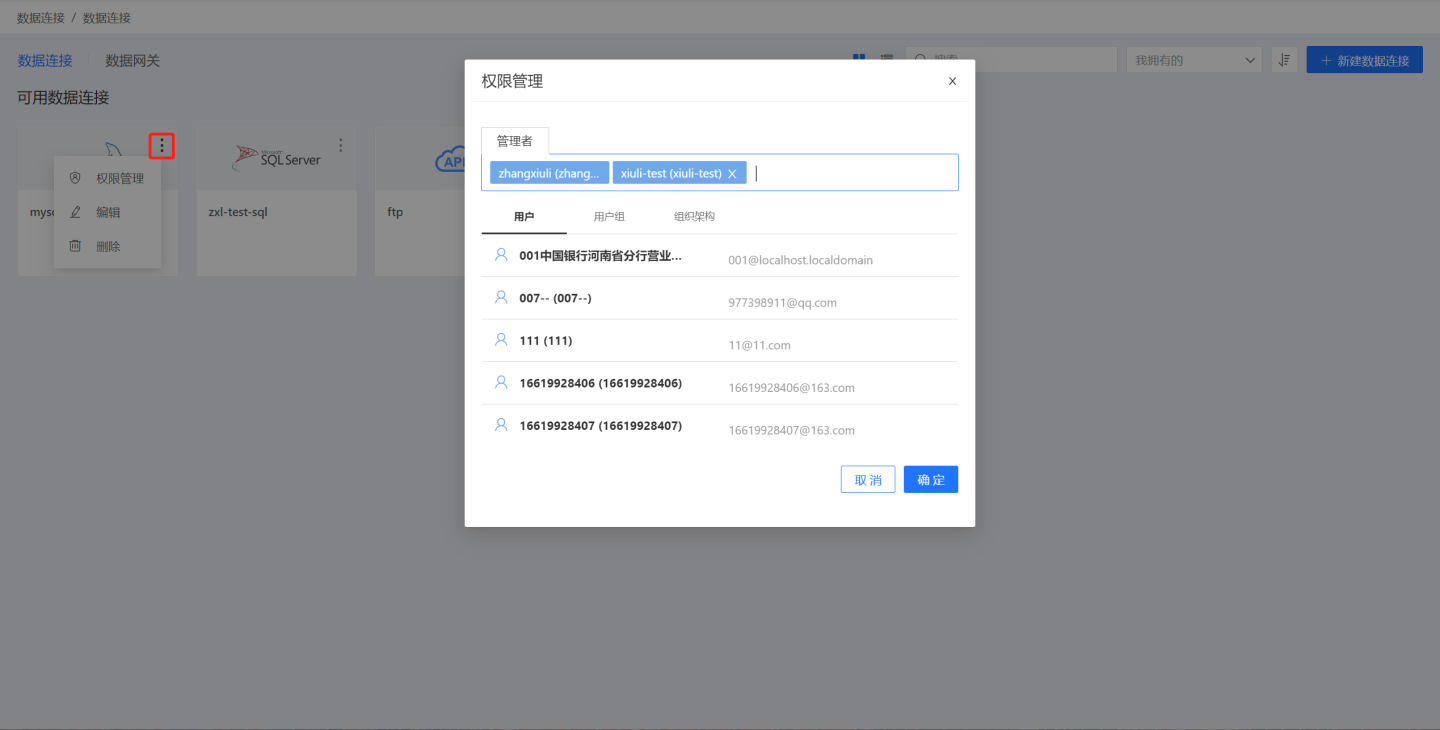
Data connection creator (referred to as the owner below) creates a data connection and can set up connection administrators to further distribute the data.
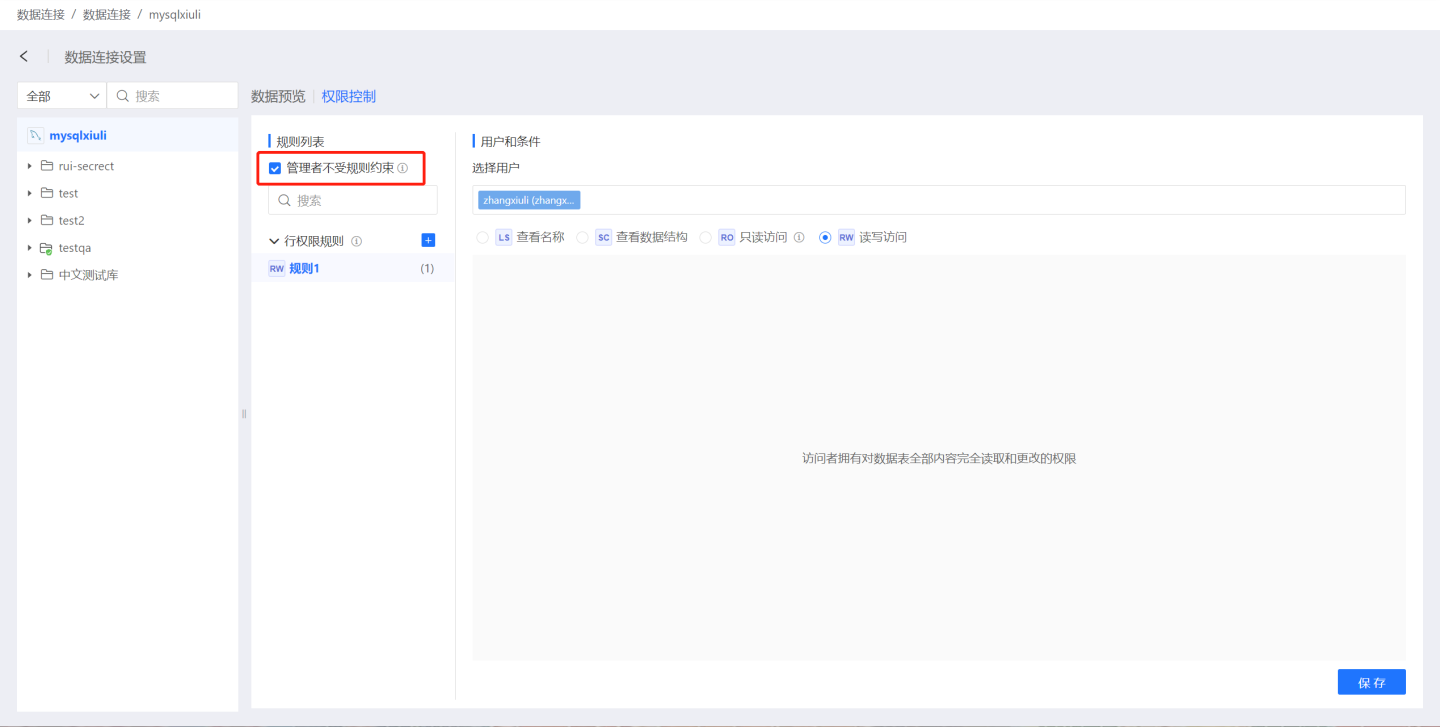
Managers are subject to rules
The connection includes administrator constraint settings, indicating whether the connection owner and administrators are subject to the rules set by the connection. By default, administrators are subject to these constraints. This feature can only be set by the owner and cannot be set by administrators.
Data Connection Owner and Manager
Data connection owners and managers have different responsibilities. The data connection owner manages the entire data connection, including creating, editing, deleting connections, setting rules for distributing connections, setting connection managers, and managing constraints for managers. Connection managers only assist the owner in distributing data and establishing data usage rules.
Connection Permissions
Both the Data Connection owner and Data Connection administrators can set connection rules and configure user permissions. Below is a detailed introduction to connection permissions.
- Data Connection Content List
- Data Preview
- Permission Control
Data Connection Content List
To help users easily and quickly find the tables they need, HENGSHI SENSE has added a search function that allows users to search by All, By Authorized, By Unauthorized, and By Visitor.
Only the owner (creator of the connection) has a dropdown list in front of the search box, which can be filtered by the above four methods.
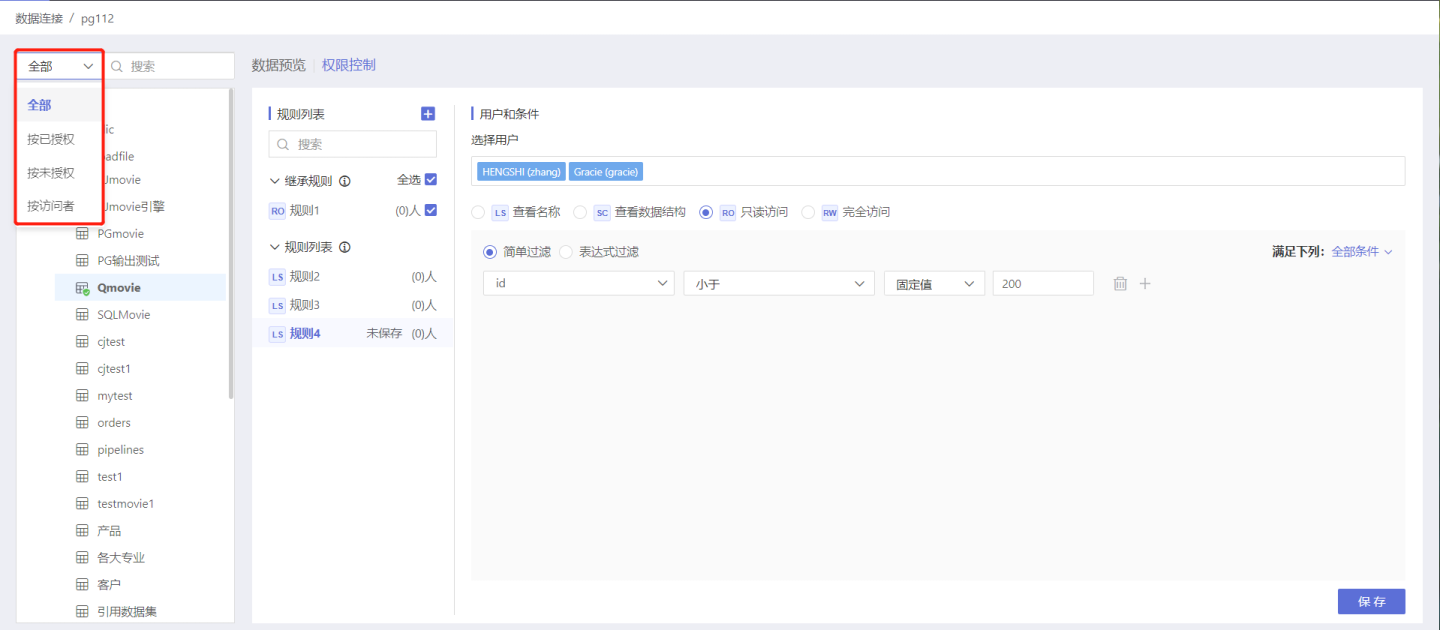
For authorized users, there is no dropdown list in front of the search box, and they can only filter from all authorized tables.
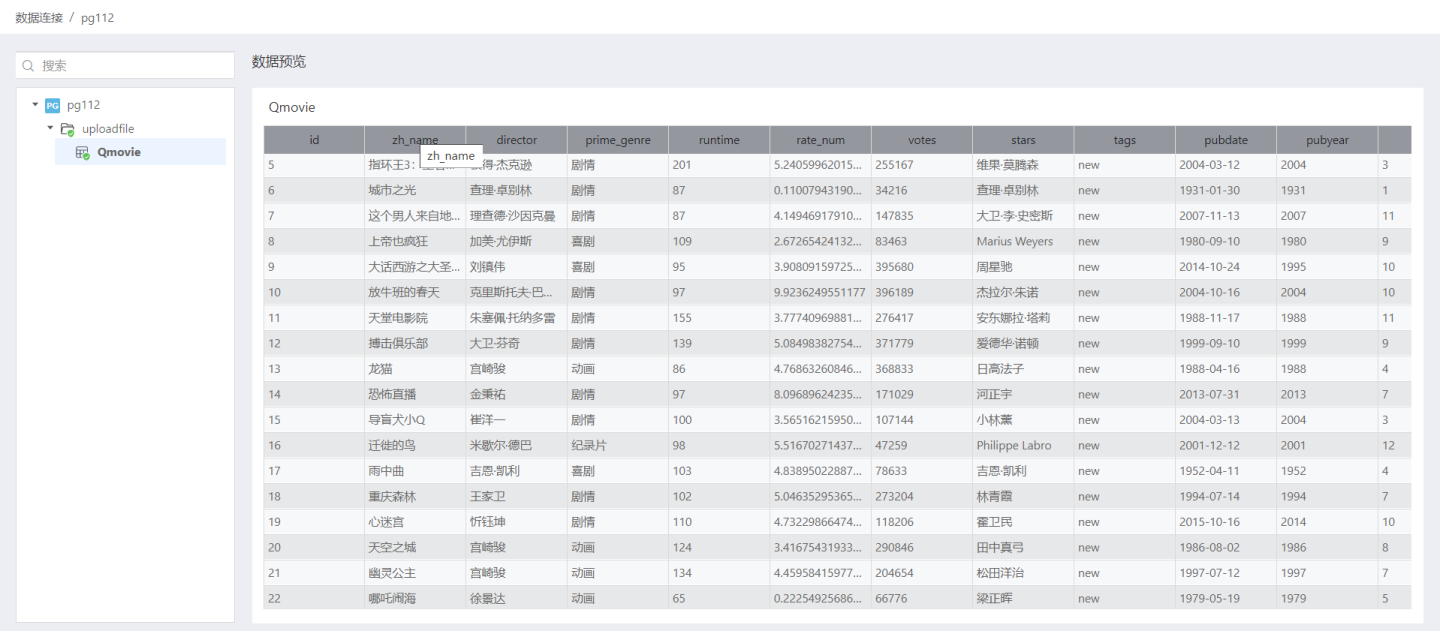
All
Search defaults to filtering from all tables in the connected database. Below lists all directories in the connection, and expanding a directory displays all tables in the connection. Simply enter the name of the table you want to find in the search box to retrieve that table. 
By Authorized
Select By Authorized and all authorized directories will be listed below (if no rules are set for the directory but there are authorized tables under it, the directory will also be displayed). Expand the directory to show all authorized tables in the connection. Authorized directories or tables will have a green icon below them. Enter the name of the authorized table you want to search for in the search box to retrieve the table. 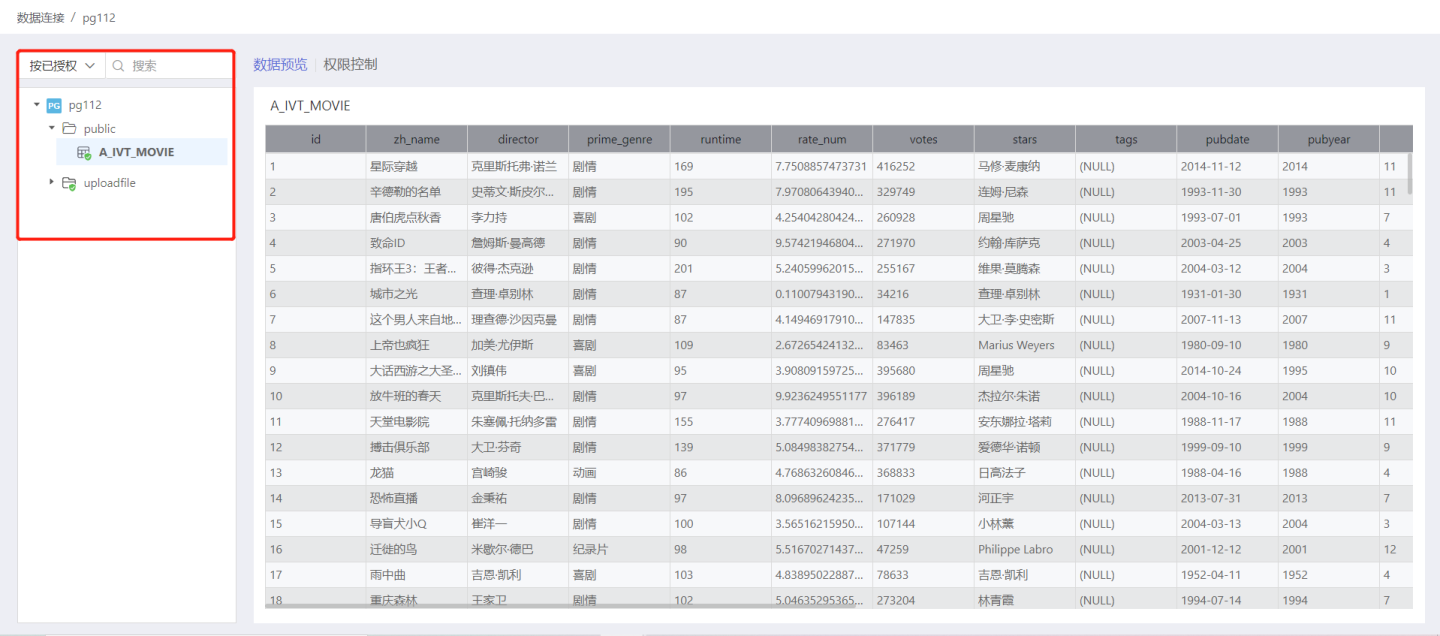
Unauthorized
Select Unauthorized and all unauthorized directories will be listed below (if no rules are set for the directory but there are unauthorized tables under it, the directory will also be displayed). Expand the directory to show all unauthorized tables in the connection. Enter the name of the unauthorized table you want to search for in the search box to retrieve that table. 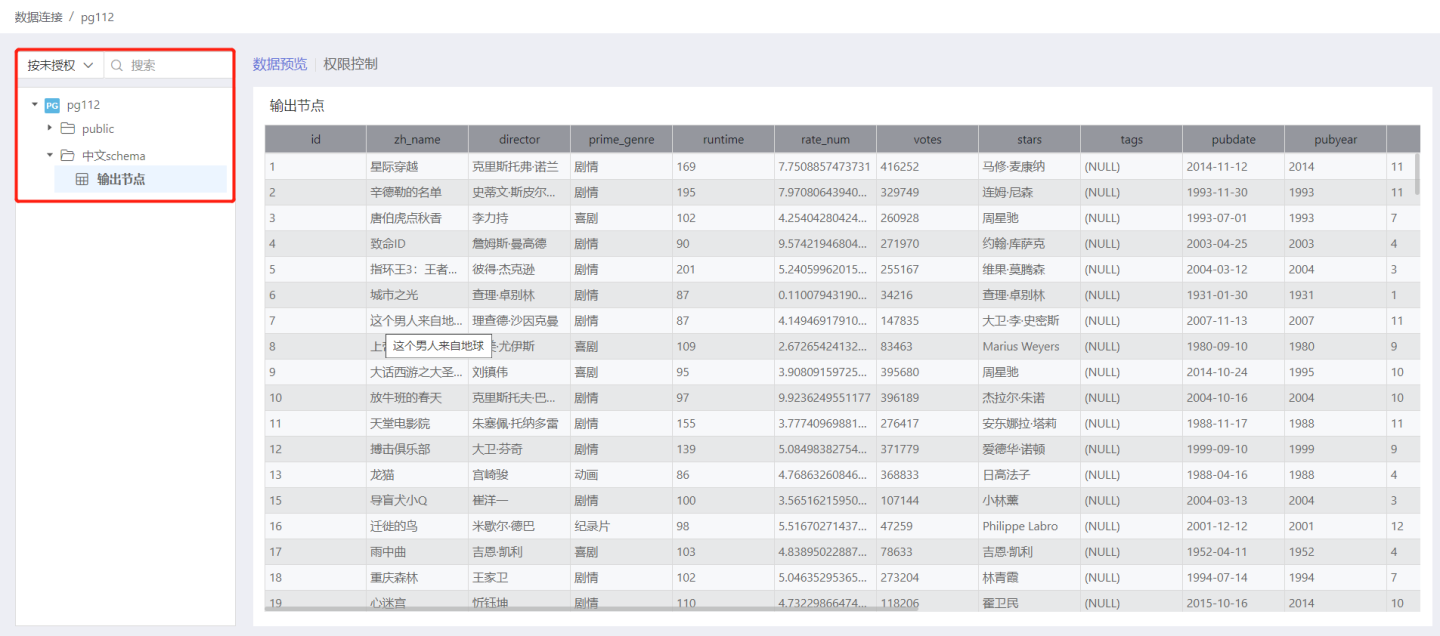
By Visitor
Select By Visitor and the list below will display all directories in the data connection. Expand the directory to show all tables in the connection. Enter the name of the user/user group you want to search for in the search box to view the directories and tables that the user/user group can see. 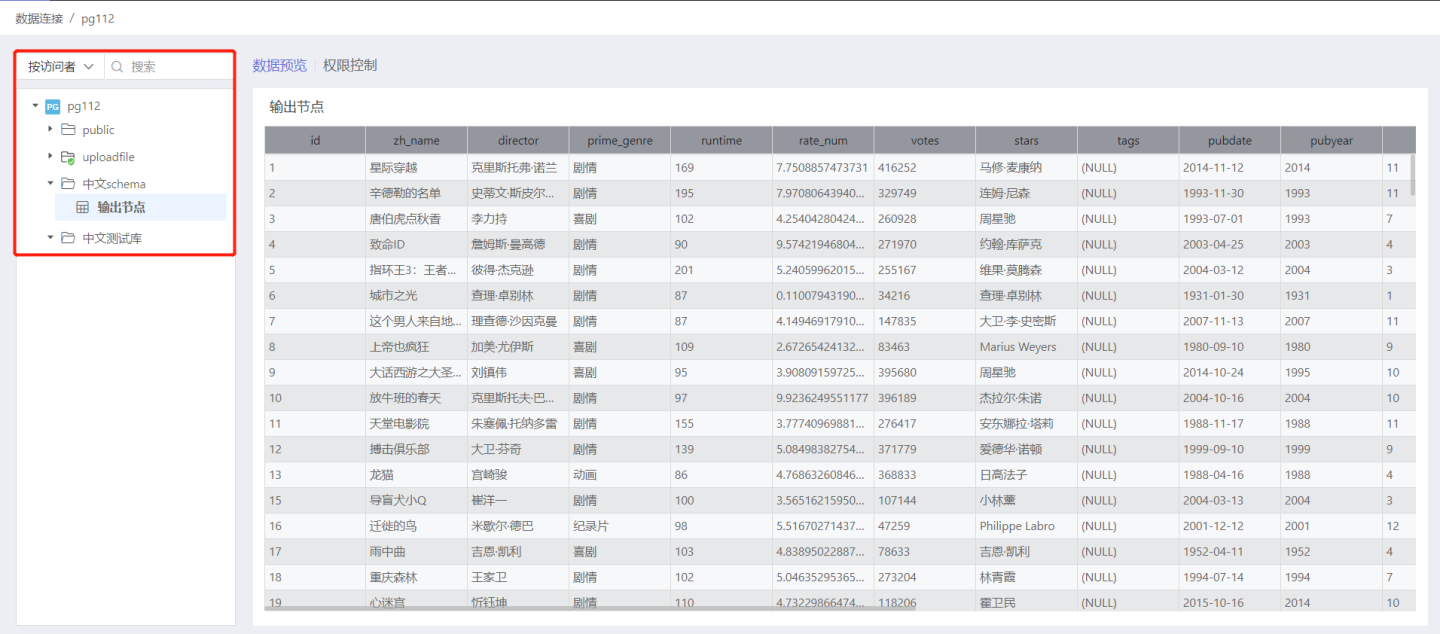
Data Preview
Users can view the data of the selected table in the data preview.
View Data as Owner
In the data connection, the owner can view all data in the tables within the data connection they created.
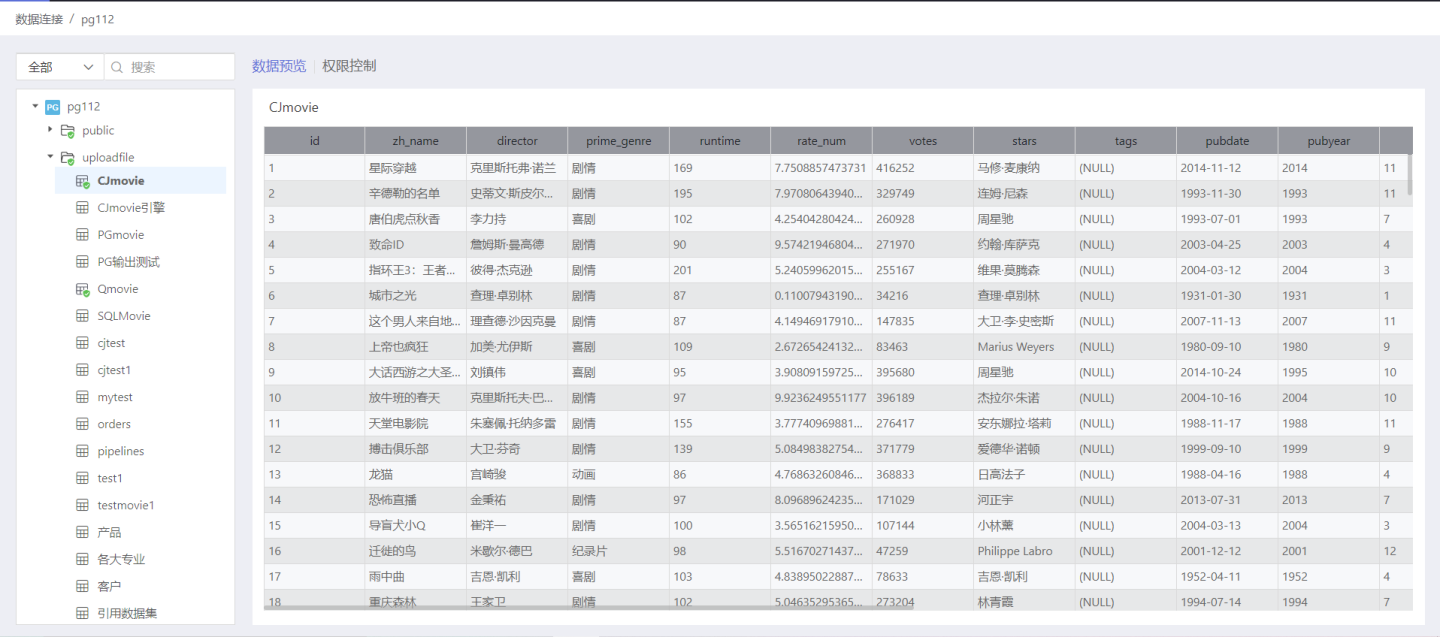
Authorize Users to View Data
Authorized users can see the data after the data owner sets the rules. The viewing permissions are determined by Authorization Type.
Permission Control
Controlling permissions for data connections enables data distribution, where the owner can add rules to determine which users can access the data within the data connection. Each rule consists of the authorized user and the authorization type.
Tip
- Only the owner can set permission control, other users do not have the permission control tab when opening the data connection.
- You can set one or more rules for the connection, directory, or table, and each rule can only choose one Authorization Type.
- Inheritance rules only apply to the rules set by the parent directory, and you can choose to inherit or not to inherit. For detailed explanations of inheritance rules, refer to Inheritance Relationship.
Authorized Users
Authorized users can grant permissions to users and user groups within the system.
Authorization Types
Authorization types include View Name (LS), View Data Structure (SC), Read-Only Access (RO), and Full Access (RW). Data connections, catalogs, and tables all support the above four types. The specific authorization scope is as follows.
View Name (LS)
- When setting up a connection, you can access the names of all directories and tables under that connection.
- When setting up a directory, you can access the names of all tables under that directory.
- When setting up a table, you can access the name of that table.
View Data Structure (SC)
- When setting up a connection, you can access the names of all directories, tables under the connection, and the structure of the tables.
- When setting up a directory, you can access the structure of all tables under that directory.
- When setting up a table, you can access the structure of that table.
Read-Only Access (RO)
- When setting up a connection, you can access the names of all directories, tables, and the structure and data of the tables under that connection.
- When setting up a directory, you can access the names, structure, and data of all tables under that directory.
- When setting up a table, you can access the name, structure, and data of that table. The RO (Read-Only) access for the table is different from other authorization types and allows for row and column permissions to be set.
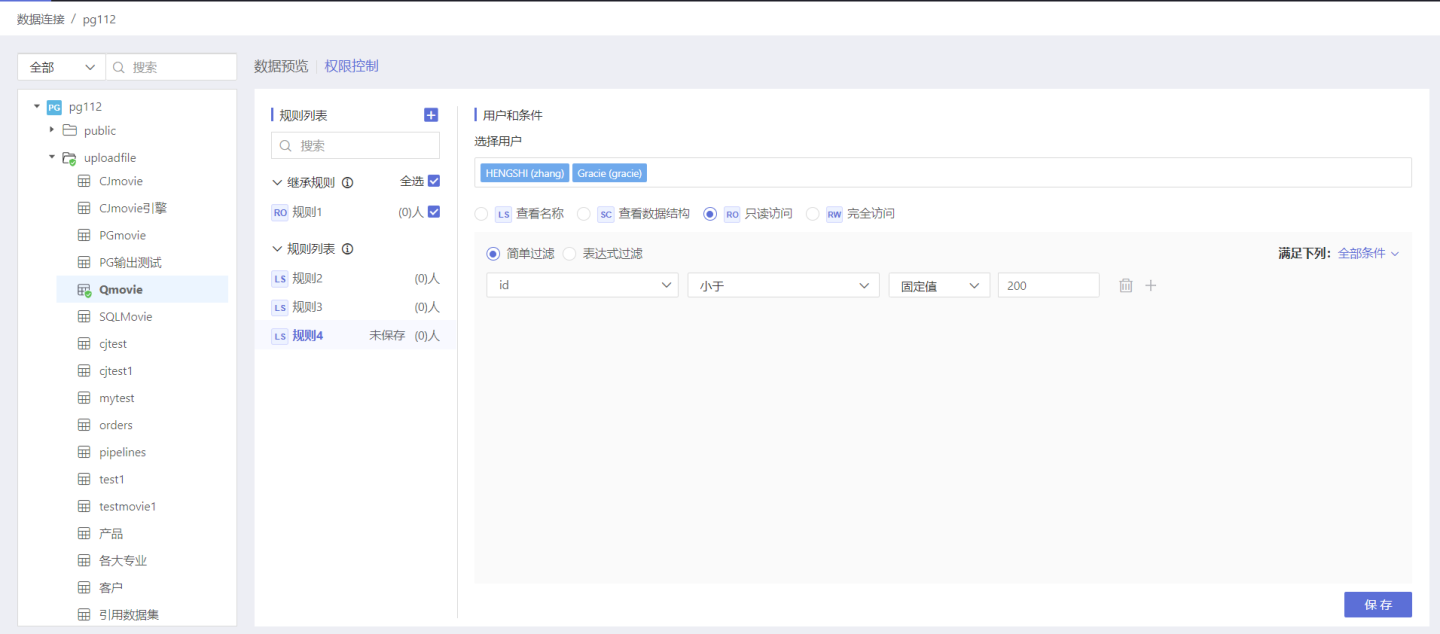
When setting row permissions, you can filter data using three methods: simple filtering, expression filtering, and SQL expression filtering, and specify which users can view the filtered data.
- Simple Filtering In simple expressions, row permission control can be set through fixed values and user attributes. When there are multiple simple filtering conditions, the rule can be set to meet 'all conditions' or meet 'any condition'.
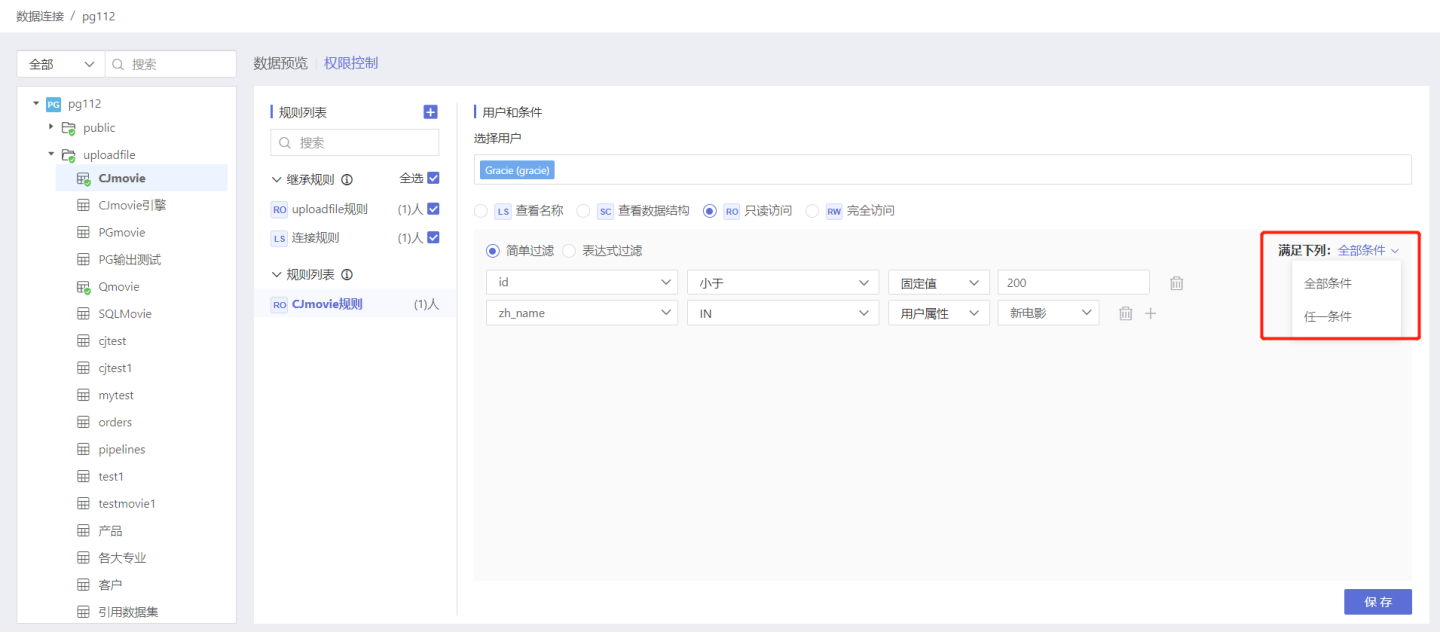
- Expression Filtering Permission control can be achieved using expressions, which are more flexible than simple filtering. As shown in the figure, the user can only see data where the regional manager matches the system username.
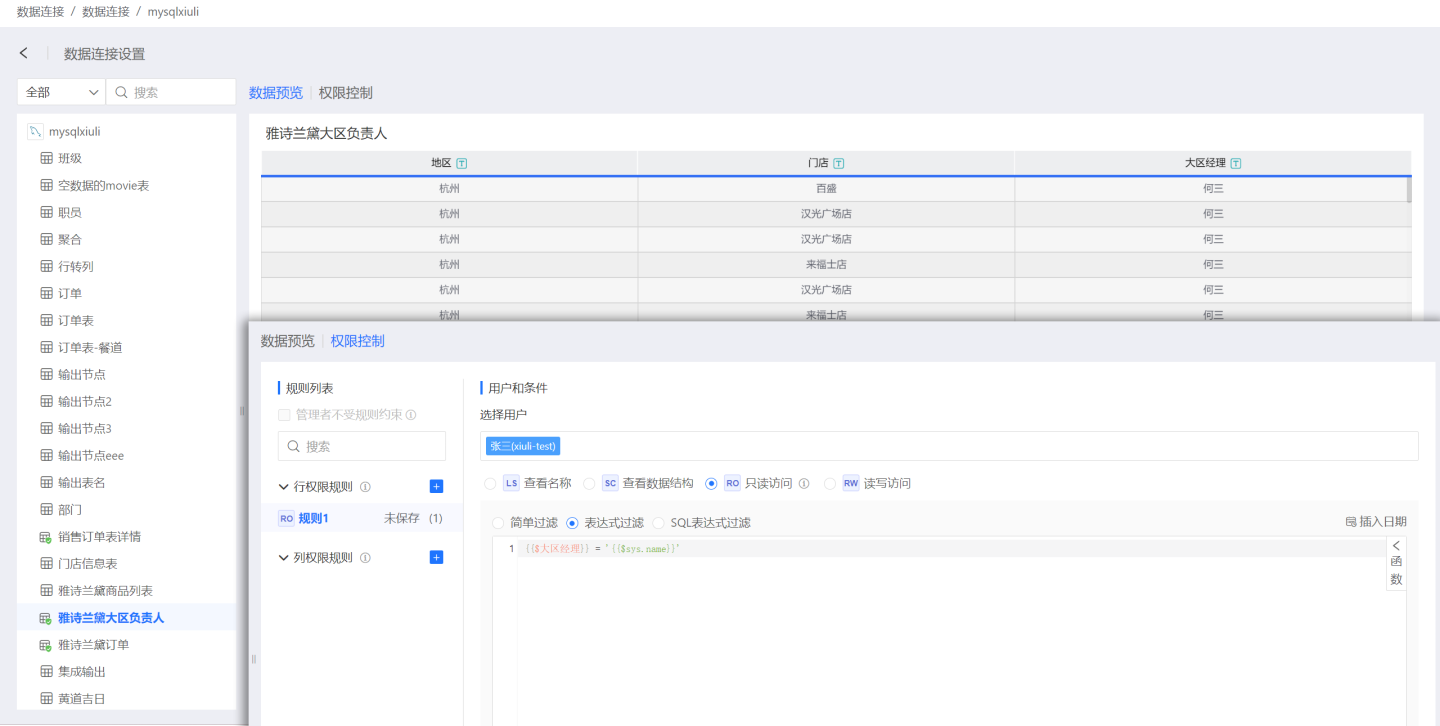
- SQL Expression Filtering Data filtering can be achieved through SQL, commonly used for cross-table permission control and complex scenario filtering. As shown in the figure, when a user views the order table, they must first see which regions they are responsible for in the regional manager table to view the corresponding information in the order table. If the user does not have corresponding region information in the regional manager table, there will be no data to view in the order table.
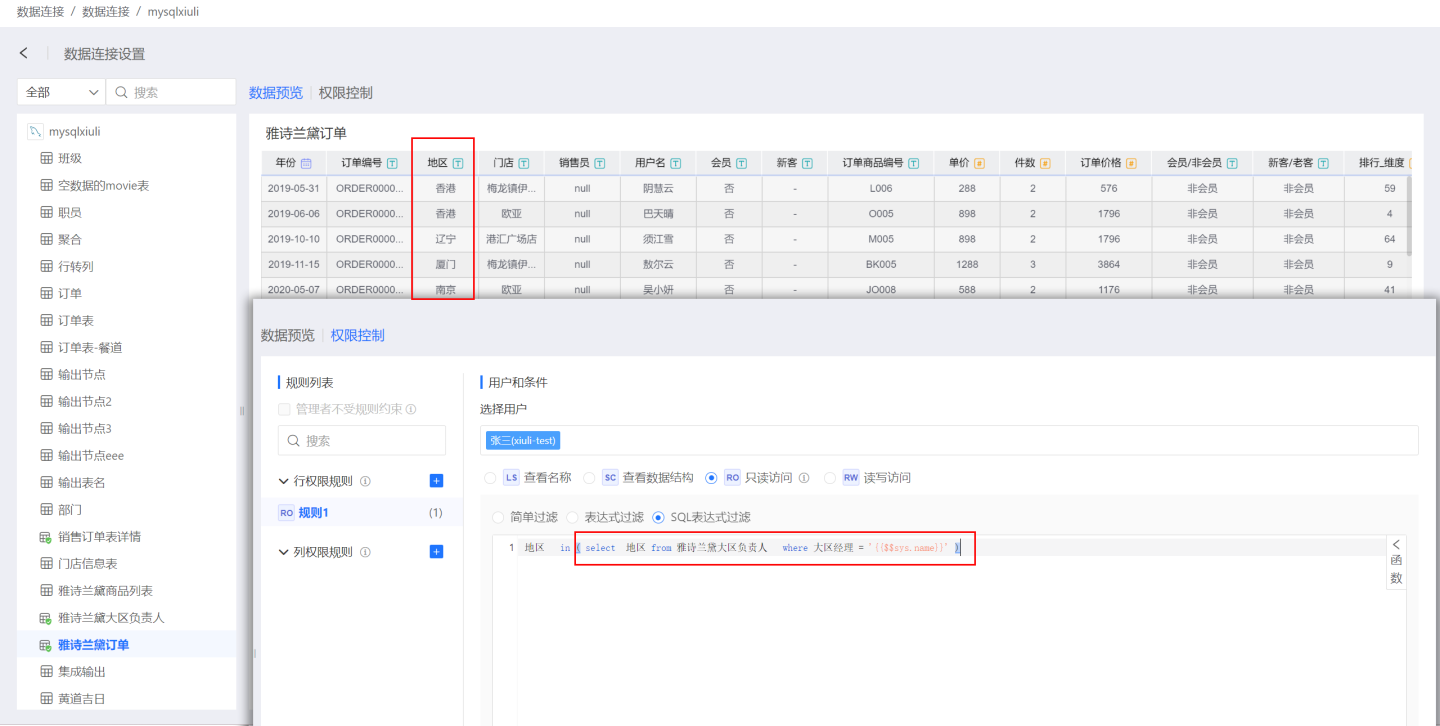
Tip
- When using expressions, please pay attention to the usage of fields and user attributes.
- SQL expressions can achieve cross-table data filtering, while simple filtering and expression filtering can only perform data filtering within the current table.
Set column permissions to determine whether the column fields are visible to users. After creating a column permission rule, specify that the user cannot view the content of the column fields in the rule. For example, if a column permission rule is set for user Zhang San, then when Zhang San views the connection, he will not see information related to the columns such as Year, Order Number, Region, Store, etc. 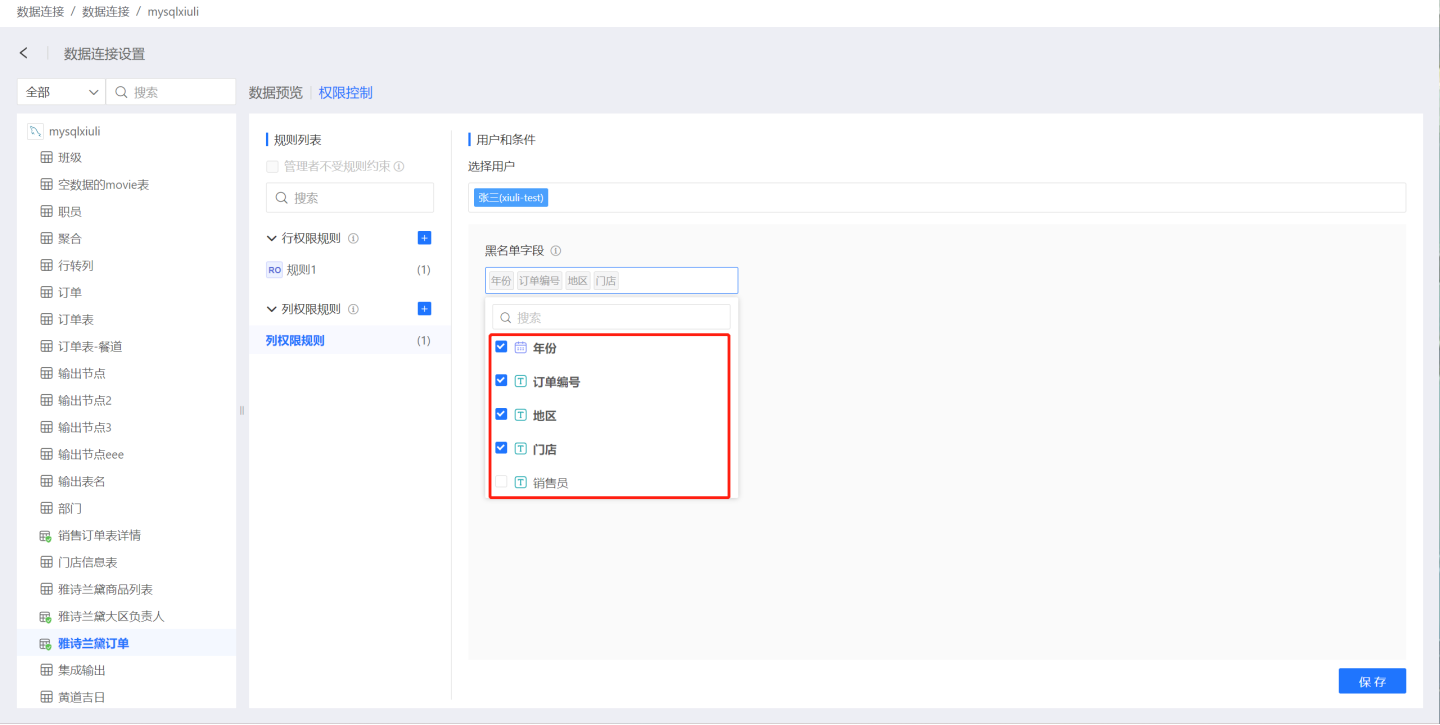
Full Access (RW)
- When setting up a connection, you can access and modify the names, structures, and data of all tables under that connection.
- When setting up a directory, you can access and modify the names, structures, and data of all tables under that directory.
- When setting up a table, you can access and modify the name, structure, and data of that table.
Add Connection Rule
Below is a demonstration of adding rules to the connection and the authorization status after the rules take effect. Step 1: Add Rules
In the data connection selection, open the Permission Control list on the right, click + to add a rule. An empty rule is generated in the rule list, modify the rule name to better align with the business logic. 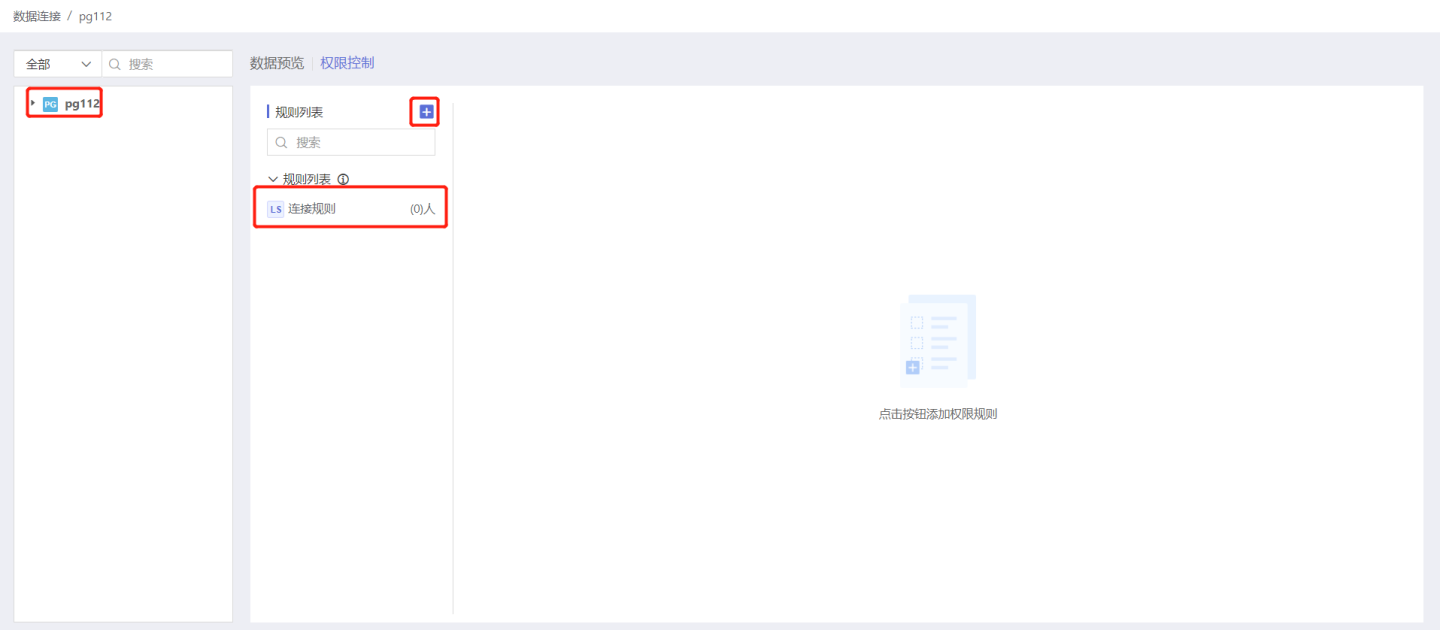
Step 2: Select Authorized Users and User Groups
Select the user/user group to which this rule applies, scroll the scroll bar of the vertical axis, and click the user/user group list to add. 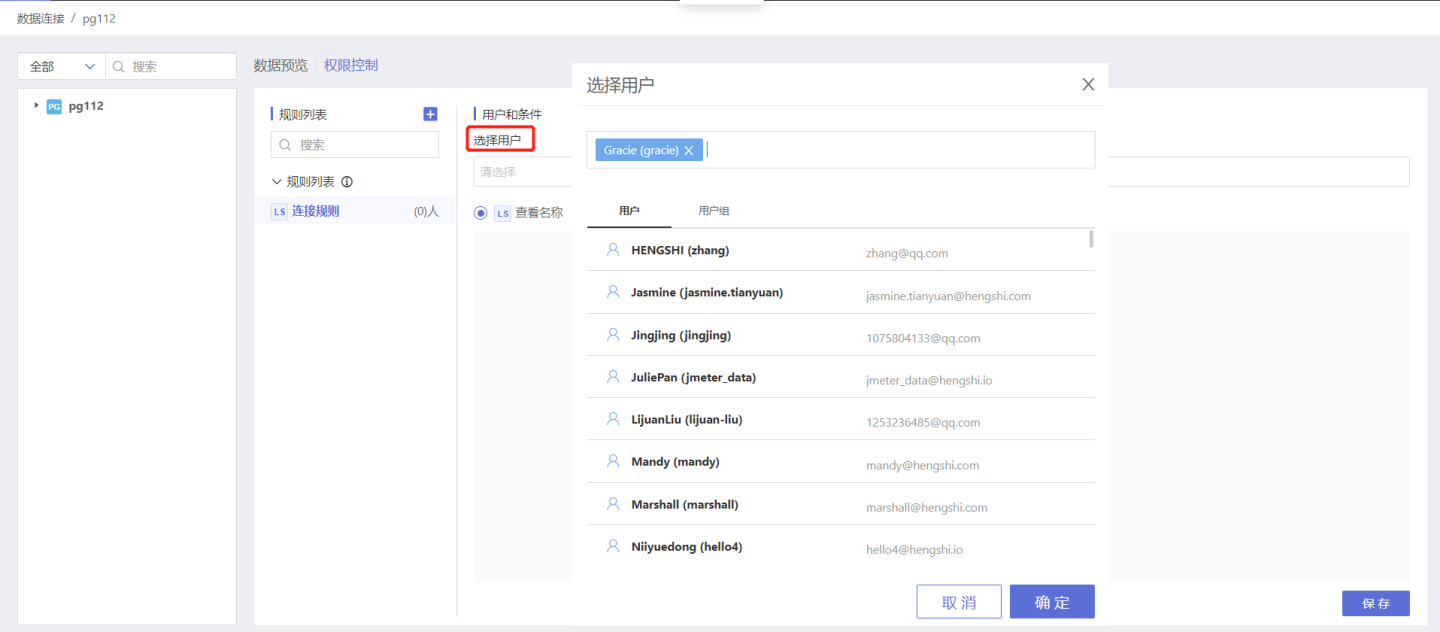
Tip
If you choose all users, you can add ALL_USERS from the user group.
Step 3: Select Authorization Type
Based on your needs, add the corresponding Authorization Type to the connection, here selecting the view name.
Step 4: Save Rules
Click Save, the rule setting is successful, and the number of users/user groups authorized by the current rule follows the rule name.
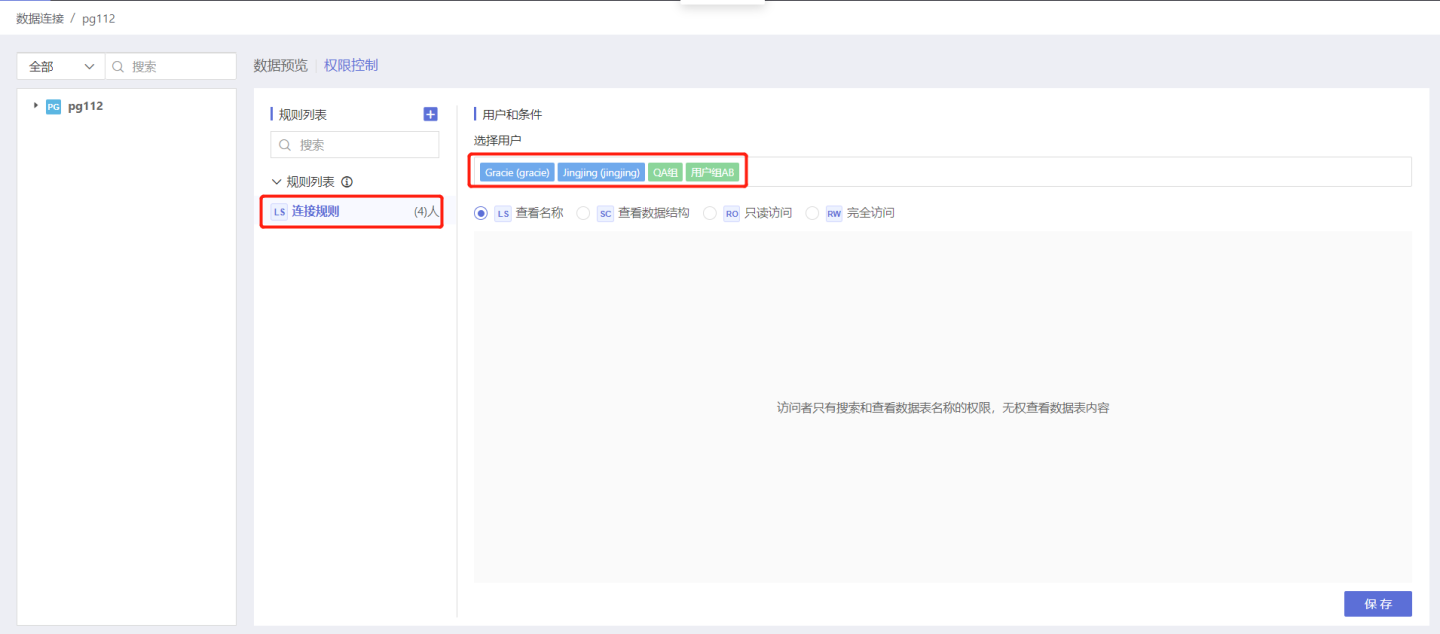
Authorize Users to View Data
Authorized users can see all the directories and table names under the connection level in the data connection. 
Tip
- Each rule supports selecting one authorization type.
Add Table of Contents Rules
Below is a demonstration of adding rules to the directory and the authorization of users to view the situation after the rules take effect. Step 1: Add Rules
In the data connection, select the directory that requires authorization, open the Permission Control list on the right, and click + to add a rule. An empty rule is generated in the rule list, modify the rule name to better align with the business logic.
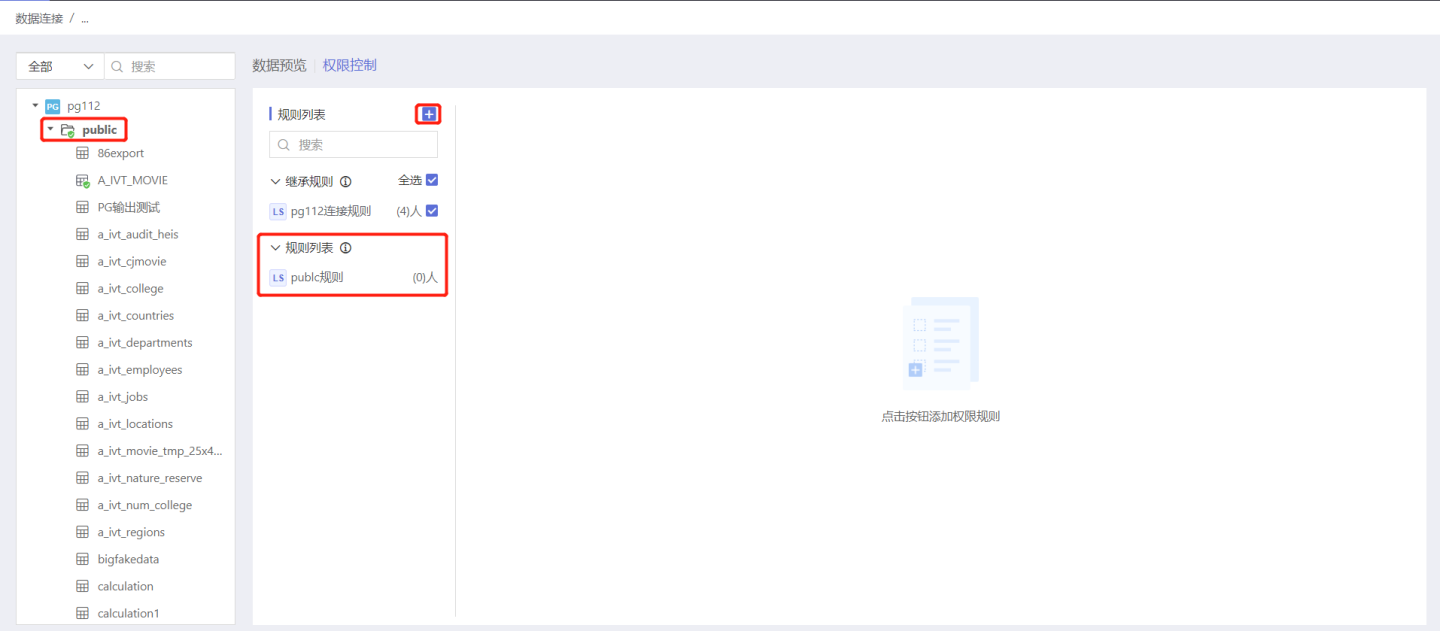
Tip
The inheritance list displays the inheritance rules, which are all the rules of the parent directory level. By default, the rule is inherited. You can also choose not to inherit.
Step 2: Select Authorized Users and User Groups
Select the user/user group for this rule to take effect, scroll the scroll bar of the vertical axis, and click the user/user group list to add.
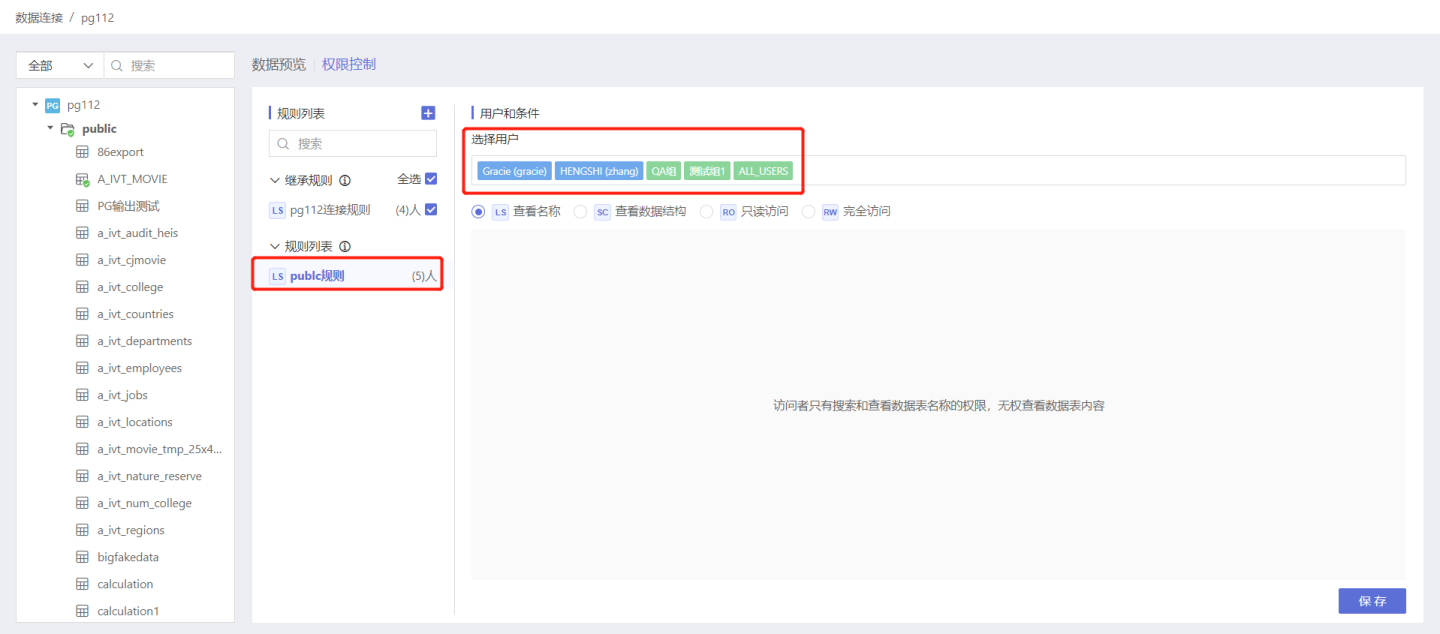
Tip
If you choose all users, you can add ALL_USERS from the user group.
Step 3: Select Authorization Type
Select the corresponding License Type as needed. Here, select the read-only access type.
Step 4: Save Rules
Click Save, the rule setting is successful, and the number of authorized users/user groups within the current rule is displayed after the rule name.
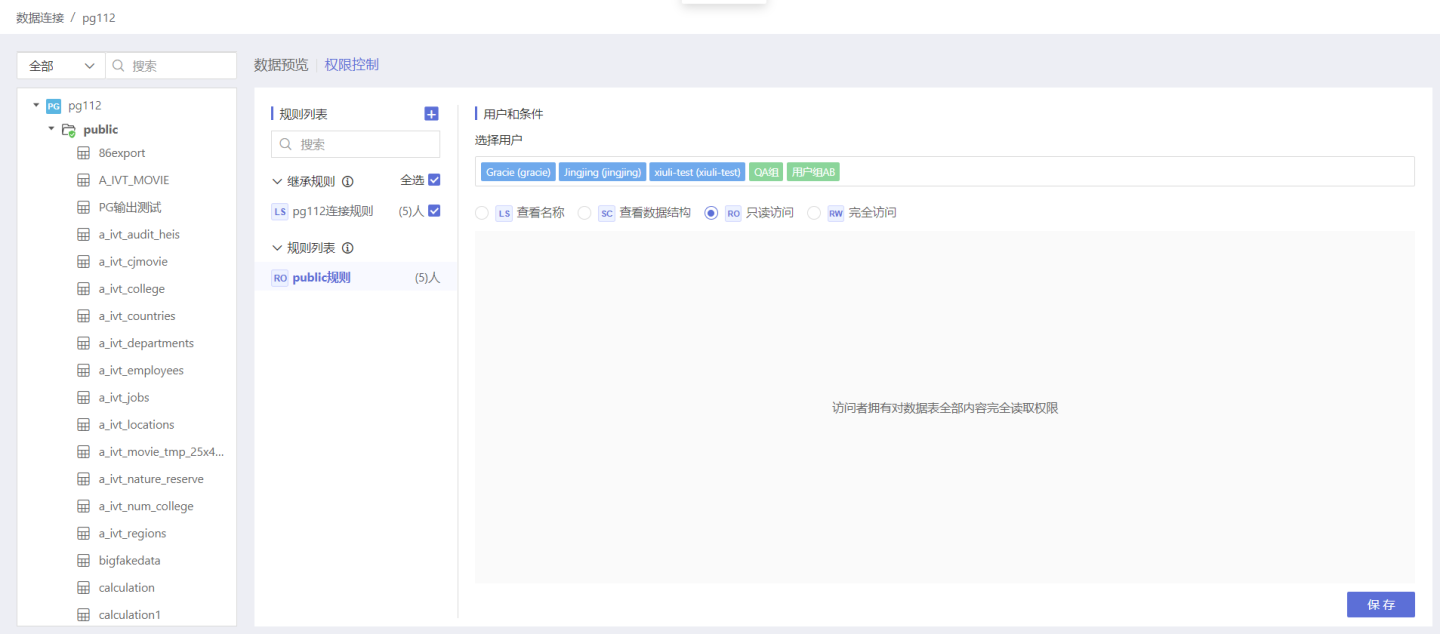
User Access After Authorization
Authorized users can see the names, structures, and data of all tables under this directory. 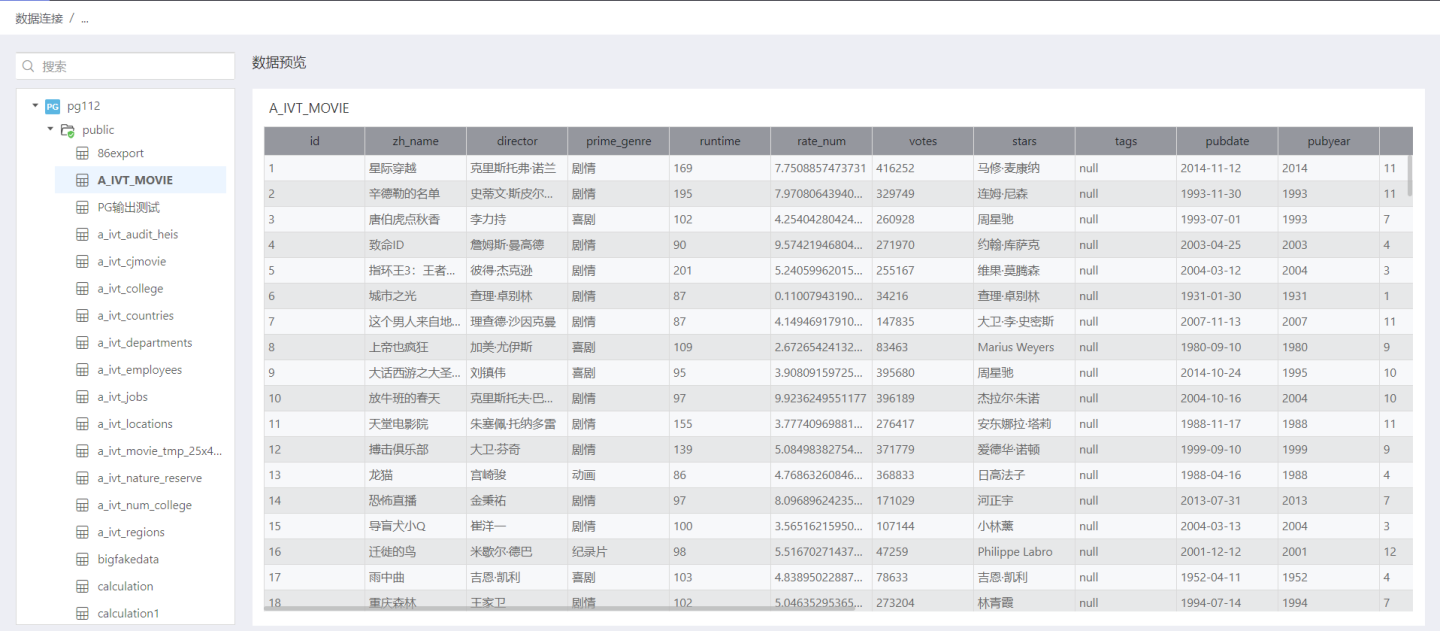
Add Table Rules
Below is an example of adding rules to a table and the authorization status of users after the rules take effect. Step 1: Add Rules
In the data connection, select the table that requires authorization, open the Permission Control list on the right, click + to add, and an empty rule is successfully added. Modify the name of the rule to better align with the business logic. 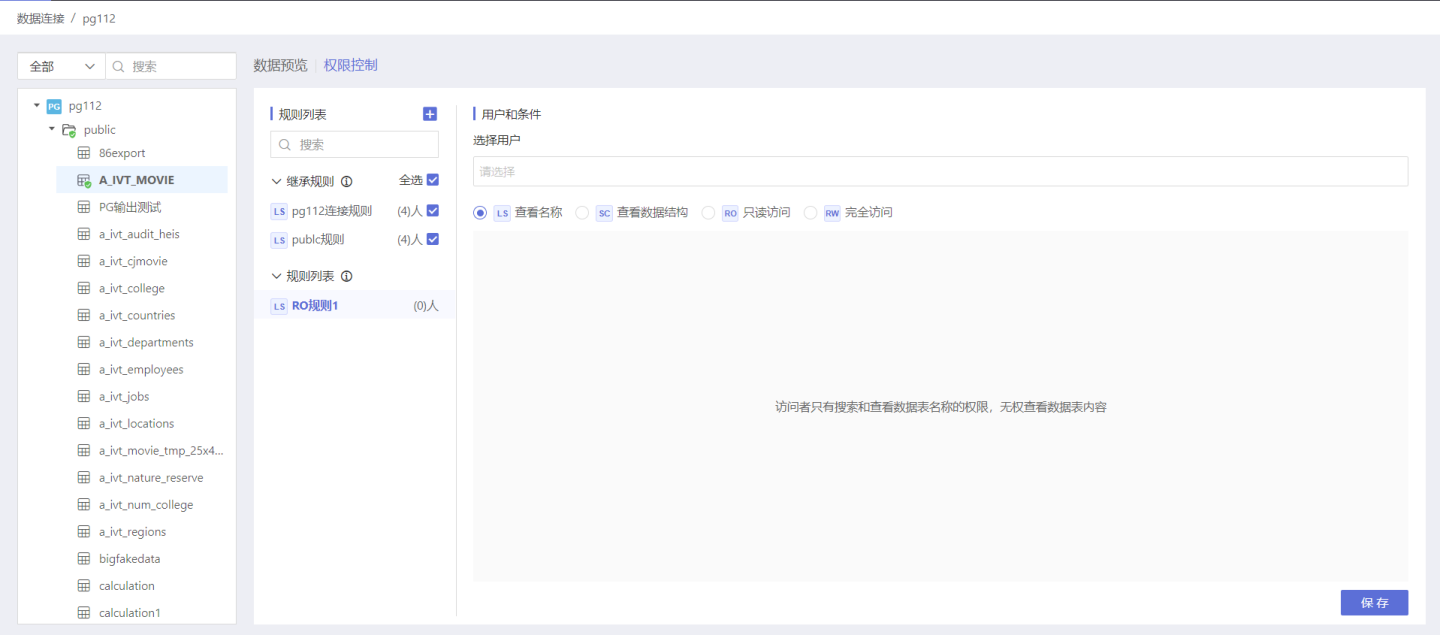
Tip
The inheritance list displays the inheritance rules, which are all the rules at the higher level of this table. By default, the rule is inherited, but you can also choose not to inherit it.
Step 2: Select Authorized Users and User Groups
Select the user/user group for which this rule applies, scroll the scroll bar of the vertical axis, and click the user/user group list to add.
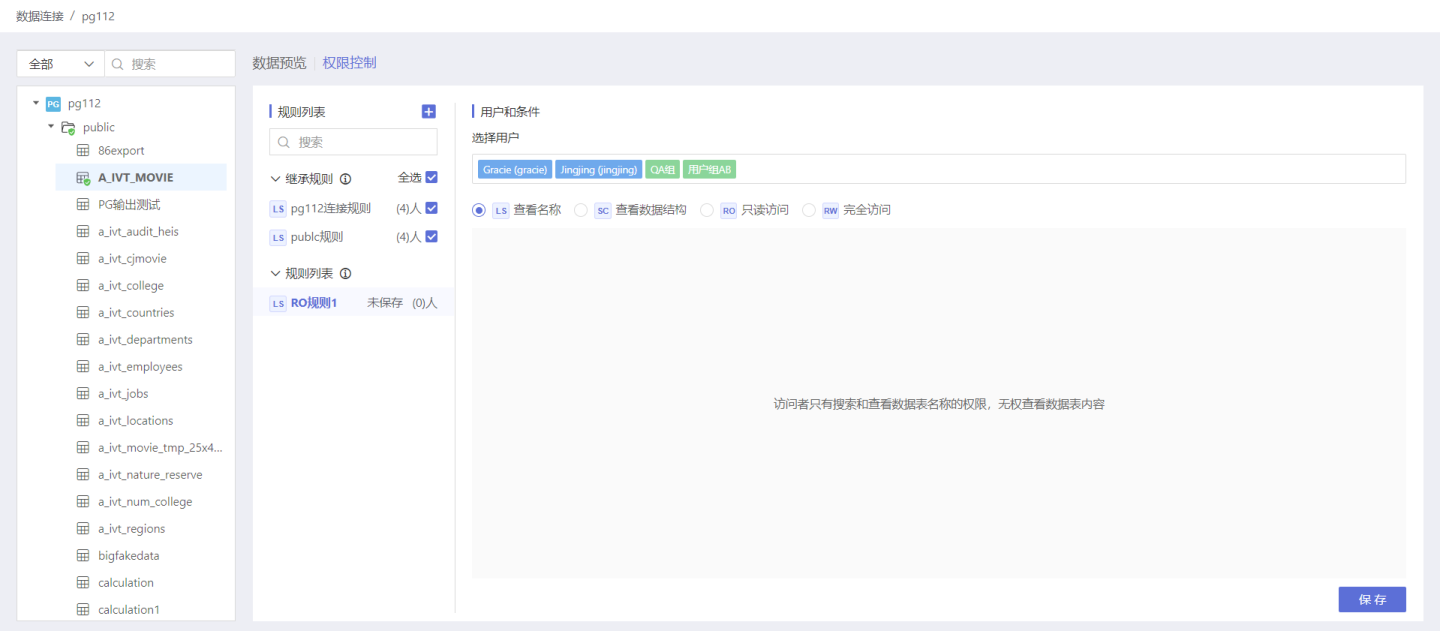
Tip
If you choose all users, you can add ALL_USERS from the user group.
Step 3: Select Authorization Type
Select the corresponding License Type as needed. Here, select the read-only access type.
Set row permissions through simple filtering.
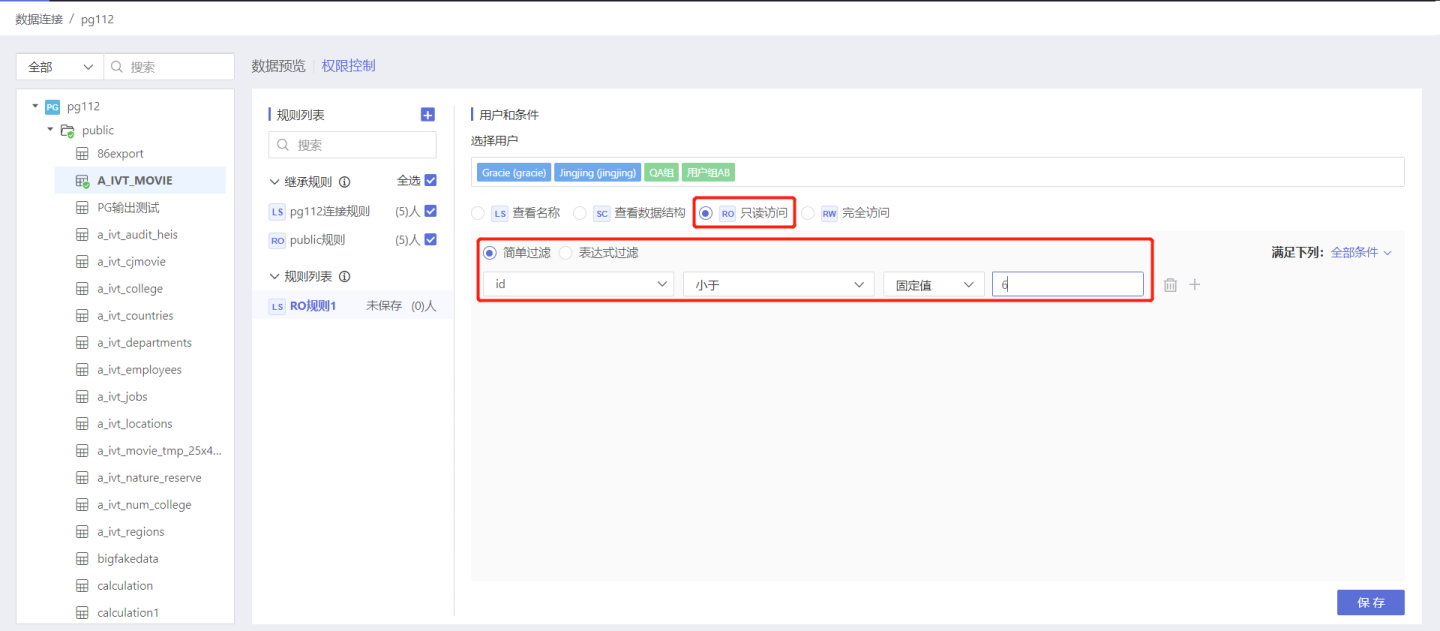
Step 4: Save Rules
Click Save, the rule setting is successful, and the unsaved update after the rule name changes to the number of authorized users/groups selected in the current rule. 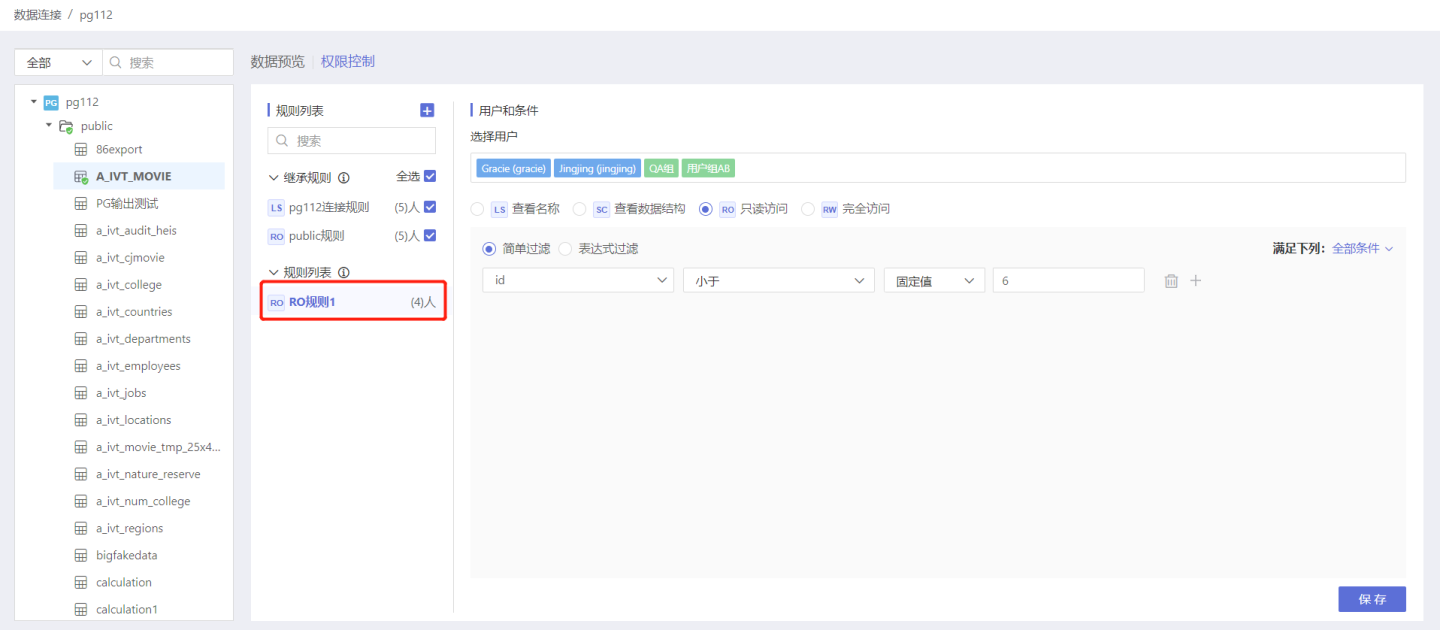
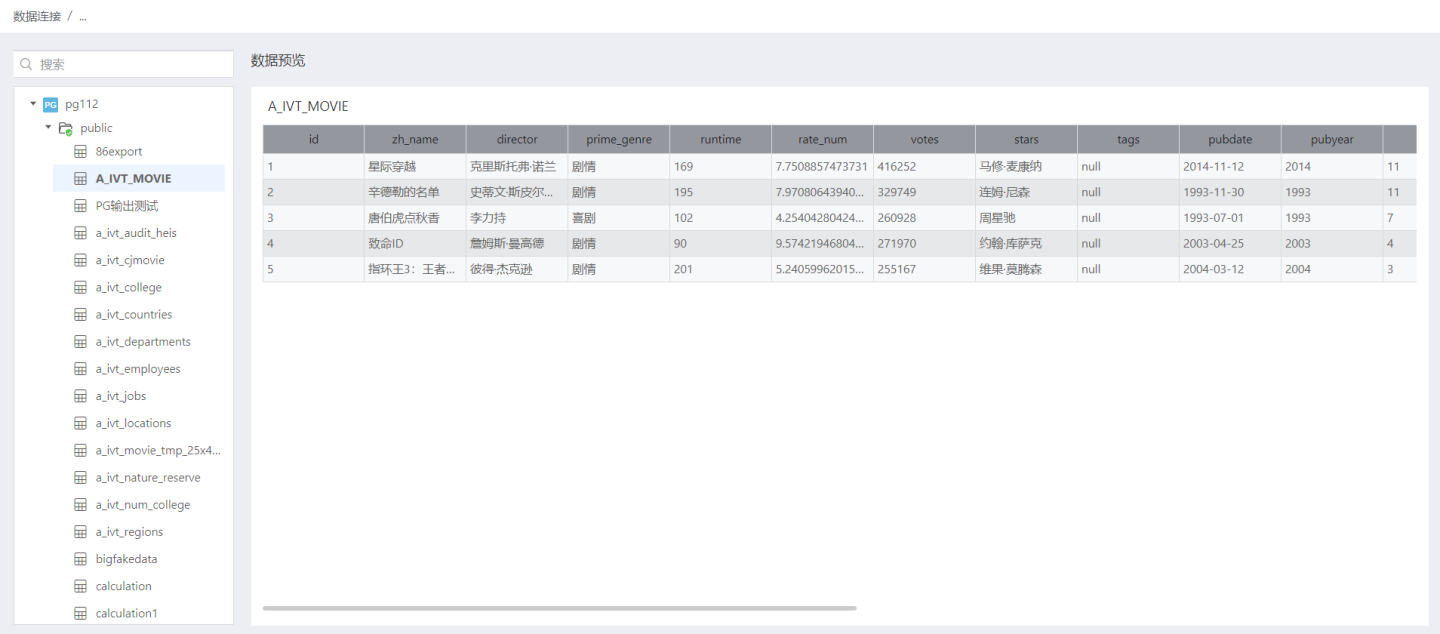
User Access After Authorization
Choose different authorization types, the content visible within this data connection when users access the app under this rule is as follows:
Relationships Between Rules
Inheritance Relationship
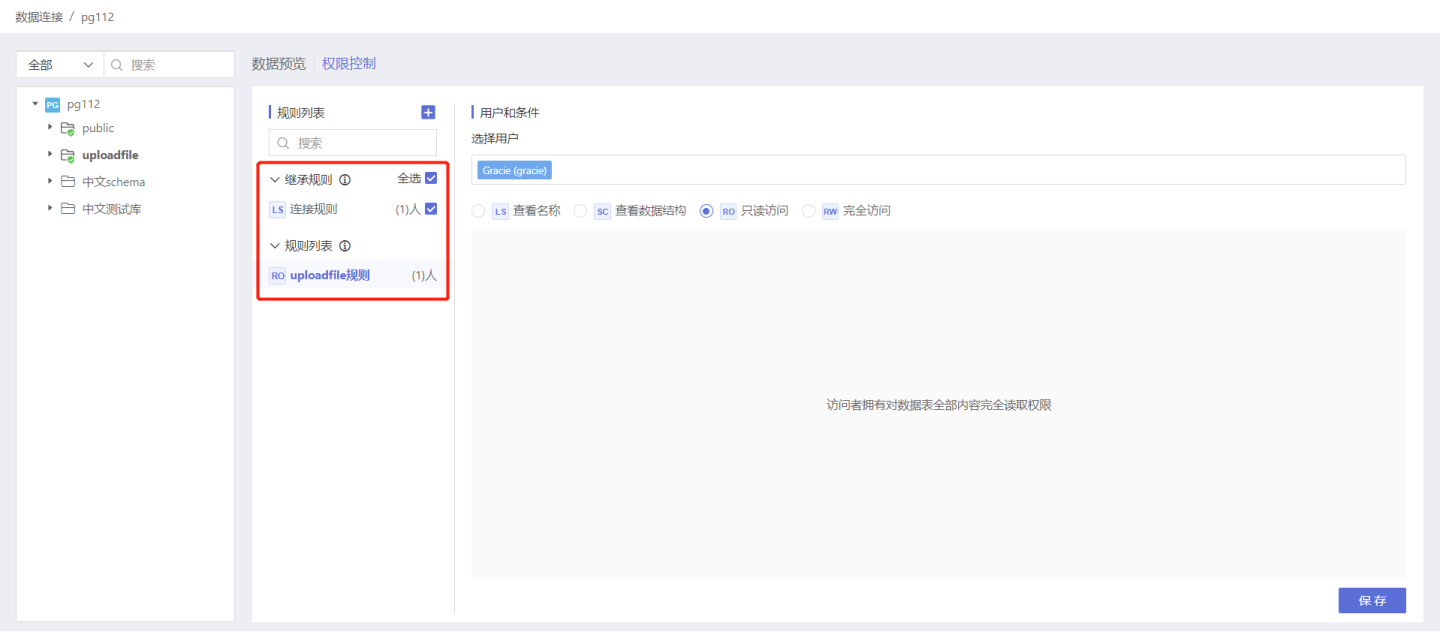
In data connection permission control, inheritance follows these rules:
- The directory will inherit the rules from its parent connection, which are placed at the top of the directory's rule list and can only be viewed, not modified.
- The table will inherit the rules from its parent directory and connection, which are placed at the top of the table's rule list and can only be viewed, not modified.
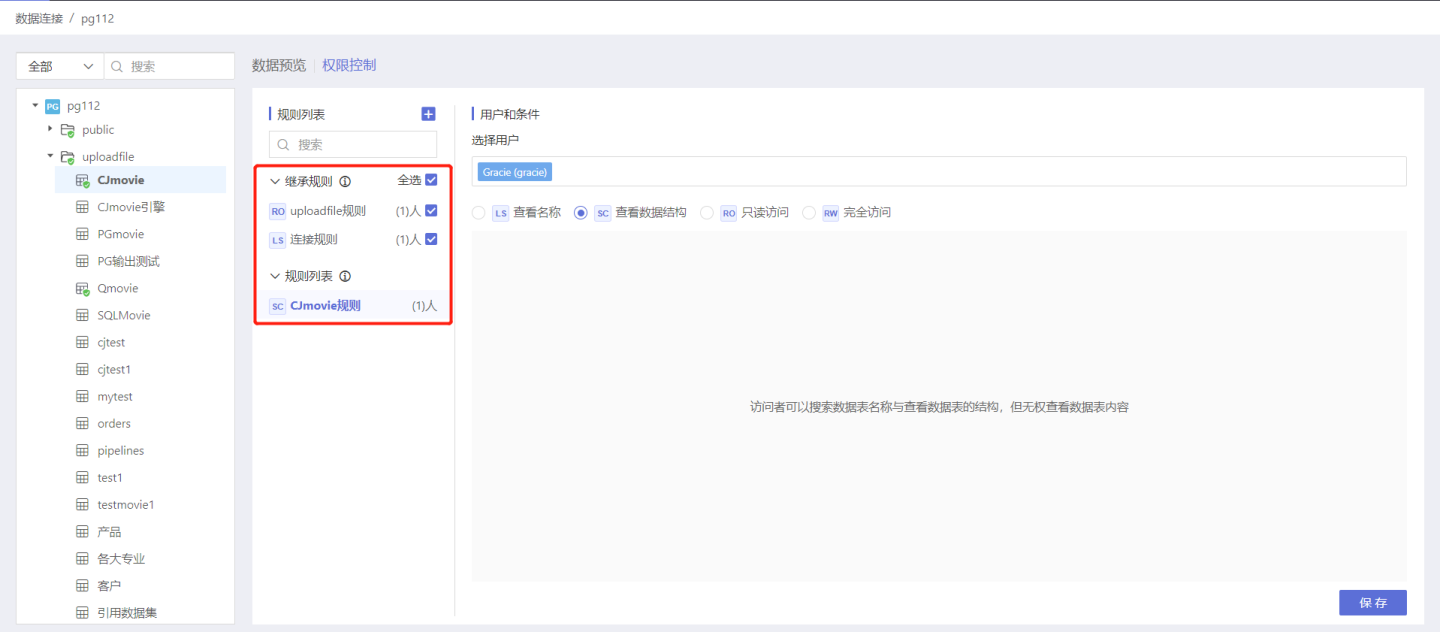
- Inherited rules from parent nodes support full inheritance, partial inheritance, and no inheritance. The default is full inheritance and effective.
- Parent node rules that are not inherited can be re-inherited by checking the box.
- When inherited rules and current rules take effect simultaneously, they are combined.
Union of Permissions
When the authorization types on the catalog and the table are inconsistent, the authorization type on the table with the larger permission takes effect.
Example: The authorization type set for user A on the directory is "View Name". The authorization type set for user A on a specific table under this directory is "Read-Only Access". Therefore, the actual permission for user A on this table is "Read-Only Access".
For the same user and the same table, if multiple rules are created, the final effective permissions are the union of the rules.
Example: For the same table, if user A is granted access to data in the "Beijing" region under Rule 1, and user A is granted access to data in the "Shanghai" region under Rule 2, user A will ultimately have access to data in both "Beijing" and "Shanghai".